北美网备份站
标题: Discuz! X3.2 实现全站 HTTPS 终极教程 [ [打印本页]
作者: 北美生活网 时间: 2017-4-5 17:36
标题: Discuz! X3.2 实现全站 HTTPS 终极教程 [
discuz X3.2在系统上是支持https的,不过需要手动修改几个地方。首先确保服务器端已开启https,且正确配置了SSL证书。
/ {* H/ D( P* Z- @
, G7 e% J! ~) v1 C: b% Ddiscuz X3.2开启支持https主要需要修改一下几个地方:
+ A9 A* ?) M0 P8 m& v8 I
1 G- x* W6 D8 ?( \* h/ b. \6 |1、查找修改文件discuz_application.php :" c3 G3 h6 q. l. a
source/class/discuz/discuz_application.php (约第 187 行处): 查找:& {8 p7 y8 ?# T4 B( ~ P9 w
$_G['isHTTPS'] = ($_SERVER['HTTPS'] && strtolower($_SERVER['HTTPS']) != 'off') ? true : false;
$ Q) ` L7 v- Z2 q w, B( }3 m _! ?! C+ V4 J! Z
# {& B! p, d9 q+ k修改为:5 I2 ]7 I @; i- K& n7 i: n
$_G['isHTTPS'] = ($_SERVER['SERVER_PORT'] == 443 || $_SERVER['HTTPS'] && strtolower($_SERVER['HTTPS']) != 'off') ? true : false;
* Y0 K# ]* f, i* s" R+ T, p% H: t4 W0 A- A% Y
8 p9 G, h: k+ k w- W$ l
2、查找修改文件avatar.php :
/ y( f: o' g, l' g$ Auc_server/avatar.php (约第 13 行处)查找:
7 [, x* m( X1 w% R; R
, y, S4 e- V% h# L- u# V1 _' N a% h W9 S; L6 e
define('UC_API', strtolower(($_SERVER['HTTPS'] == 'on' ? 'https' : 'http').'://'.$_SERVER['HTTP_HOST'].substr($_SERVER['PHP_SELF'], 0, strrpos($_SERVER['PHP_SELF'], '/'))));1 p8 E7 o9 H+ R5 E' j; `: }: L
5 M& f" D) Y% |& E
& G0 o4 Q$ J9 K1 D, R/ F; g; D
5 I. b/ O& r( j; ?( V5 r) _& G) T" F2 G
2 A3 z( H, x. @2 n: d$ s修改为:$ D8 F+ u2 a6 b5 p% C: v
define('UC_API', strtolower(($_SERVER['SERVER_PORT'] == 443 || $_SERVER['HTTPS'] == 'on' ? 'https' : 'http').'://'.$_SERVER['HTTP_HOST'].substr($_SERVER['PHP_SELF'], 0, strrpos($_SERVER['PHP_SELF'], '/'))));7 H0 G6 ?: d2 P# e% Z* n, T
* u6 y( u; P2 \1 Z% T
+ {6 b: K4 o* o, G
3、除去非 HTTPS 内容避免提示”不安全内容“
1 C: E5 f- B9 F& t+ Y2 O4 DSource/plugin/manyou/Service/DiscuzTips.php ,最后的那段 JS 加载脚本删除就行。2 B8 x/ n7 u' D0 U- O
非楼主层如果有点评,那么点评者头像不是 HTTPS 开头,也需要修改一个文件来适配: template/default/forum/viewthread_node_body.htm (约 180 行),搜索 div class="psta vm">,将下面一行注释掉或者删除。
8 k Y$ I; G0 R6 S6 S打开浏览器,使用开发者工具或者查看源码逐一排查加载的非 HTTPS 资源并修改。1 h/ O& Q- j) G; O
, V) l1 p7 L$ |- F% z& H$ G4、后台设置的修改完善+ p5 W* ~ r; O! [! I! y% Y* F
在后台还有一些设置,可能会干扰 https 的使用。" {3 A: Q8 V# H! H
% j$ Q, S5 K, {! g, d! R% @. x7 D- W
后台 >全局 > 站点 URL ,改为 https 开头的. Q+ q+ l& H) _$ W" x! k
6 g$ [, }1 K1 [( Q7 y3 N4 C) M后台 > 站长 > UCenter 设置 > UCenter 访问地址,修改为 https 开头的
! D) p: \( O1 q" J: q* ?
+ d! a4 _# N7 w* f$ C; f. l XUCenter 后台 > 应用管理 > 应用的主 URL ,修改为 https 开头。
' W. }! X% S1 d0 S修改后可能会显示通讯失败,如果 UC 和论坛程序安装在同一机器,此失败可无视,实测可以和 UC 正常通讯不影响(测试是否正常通讯程序的 Bug ),如果 UC 和论坛程序不在一台机器上,有可能不能通讯。 另外在 后台 > 全局 > 域名设置 中的一些设置也可能使 https 失效,如果更新缓存后论坛默认连接还是 HTTP ,请删除 后台 > 全局 > 域名设置 > 应用域名 > 默认 里面的默认域名(一般去 forum.php 尾巴这里会有内容,为了 HTTPS 请删除)。
4 ?* I- r. e9 G: s( A" n o
- y h( e9 r: Y- W4 W% Q) V5、模板的调整 M7 M3 J$ }" z7 y ]' j
主要在模板的 foot.html 以及 header.html 等文件中,使用工具逐一排查模板文件中写死的 HTTP 链接,修改为 HTTPS 。 |* G: C7 v. ]4 K9 i9 o+ o3 i2 o
% Q- M6 Y5 f4 e6 }' k' I; {7 m: i# k+ c0 {: n
6、数据库的调整
; L7 ^5 L) D0 y* f在论坛这种交互社区中,经常回复发帖时会有出现主域名的链接,在没有 HTTPS 之前,链接都是 HTTP 开头,这个时候,我们需要修改数据库,运行下面的 mysql 命令更新数据库,将 HTTP 替换为 HTTPS :
3 C: m* c& Z" S2 {0 e' q* l进入 DZ 后台:站长 – 数据库 – 升级 p2 c! c8 z% J6 i
UPDATE pre_forum_post SET message=REPLACE(message,'http://你的网址','https://你的网址');8 P8 a' a) n7 y- C
* {: G4 S0 d7 E. j+ |- ^% F
. ~; z: {$ o7 ~- K+ Q
1 P' W7 l$ y" F- |! m* D) q需要注意的是,出于安全考虑, Discuz 后台默认情况下禁止 SQL 语句直接执行,只能使用常用 SQL 当中的内容,如果想自己随意书写 SQL 升级语句,需要将程序文件 config/config_global.php 当中的$_config[admincp][runquery] 设置修改为 1 。; N+ |2 |6 N2 Q' p1 F: d; t; m
$ \" u3 F! F* C. C$ ~9 Z7 w- [1 f- k: K2 p w. M% ^
到此,discuz X3.2已经开启支持https了 。+ N3 e/ T0 z% r4 v% ]
) _" V$ I; ]+ U0 B7 p% q1 T& X$ E/ X" @& T
当然,你还需要申请SSL证书、在服务器端部署SSL证书。* [/ A4 i8 `: E/ H) [$ q
- x C l: P L8 [" ~: o! Y3 l: ?# \. `7 O6 \! n; S
服务器端部署https的SSL证书可以看我的这个教程:6 x* G1 S! y% M, V! D
b0 C/ T4 K3 l: ]( M* ~/ D
! S7 X" C- Z7 ^6 h( khttp://www.aitiancheng.com/article-246.html
作者: 北美生活网 时间: 2017-4-5 18:02
Discuz X3.* 全站开启 SSL / HTTPS 后需解决的问题
http://www.vdazhang.com/wenzhang-1587.html/2
一、全站资源 https 化。
1、UCenter地址、本地附件 URL 地址、风格图片地址需全部开启https访问,否则浏览器会出现类似“网站内存在不安全的资源”的警告。如果这部分链接全部是相对链接,则请忽略本项。
若“风格管理”中将“界面基础图片目录 {IMGDIR}”和“扩展图片目录 {STYLEIMGDIR}” 地址设置为 https 开头的绝对链接,需要修复一处BUG,否则会导致这部分风格图片无法显示。
打开 source/function/cache/cache_styles.php ,查找以下三项:
$cssdata = !preg_match('/^http:\/\//i', $data['styleimgdir'])
; U7 B: U* l$ t* P2 N3 @7 @6 Q$cssdata = !preg_match('/^http:\/\//i', $data['imgdir'])# l7 x9 E& s4 ]
$cssdata = !preg_match('/^http:\/\//i', $data['staticurl'])将其中的 /^http:\/\//i 替换为 /^http/i ,保存覆盖。
注意:修改后,若将来要使用相对链接,需要确保目录不以 http 开头。
2、解决 DiscuzTips 造成的不安全资源提示。
打开 source/plugin/manyou/Service/DiscuzTips.php ,在 echo $jsCode; 前加 // 将其注释掉。
3、百度结构化插件暂不支持 https ,将造成浏览器提示存在不安全资源。暂停使用该插件。
4、使用浏览器的开发者工具逐一排查是否存在其他 http:// 资源(包括图片、JS、CSS的,A链接无影响)。
5、清理用户签名位中的 http:// 图片,清理帖子中存在的外链图片。
二、解决QQ互联登录问题。
截至2015年12月,Discuz的QQ互联仍不支持 https 站点,我们可以进行以下操作,将QQ互联链接调整为 http:// ,QQ互联登录跳转回 http:// 后再在站点内部301到 https:// 页面。
1、考虑到防止屏蔽等因素,建议启用一个独立域名,并在论坛所在服务器新建一个该域名的站点,站点目录中使用软链接链接论坛的以下目录:api config data source static 和以下文件:admin.php api.php connect.php ,即相当于对论坛做一个镜像但仅限于QQ互联相关文件。
2、打开 source/plugin/qqconnect/connect.class.php 文件,将 40-46 行中的:
$_G['siteurl'].'
替换为:
'http://上面创建的专用网址/
3、打开 connect.php 文件,在最前方加入:
if($_SERVER['HTTP_HOST'] != 'www.你的网址.com' || ($_SERVER['HTTP_HOST'] == 'www.你的网址.com' && $_SERVER['SERVER_PORT'] != '443')) {
header('HTTP/1.1 301 Moved Permanently');
header('Location: https://www.你的网址.com'.$_SERVER['REQUEST_URI']);
exit;
}
三、解决后台应用中心无法访问的问题
在第2步基础上,访问第2步中专用域名下的 admin.php 登录后台即可正常进入应用中心。
四、禁止在第2步专用域名下更新缓存(否则前台部分图标地址会使用该域名)。
打开 source/admincp/admincp_tools.php 文件,查找:
showtips('tools_updatecache_tips');. W i7 R9 Q# l7 C) e
! q+ x. e+ u7 e! F) \ if($step == 1) {
) ? q) |1 V. z+ o4 |6 @ cpmsg("<input type=\"checkbox\" name=\"type[]\" value=\"data\" id=\"datacache\" class=\"checkbox\" checked /><label for=\"datacache\">".$lang[tools_updatecache_data]."</label><input type=\"checkbox\" name=\"type[]\" value=\"tpl\" id=\"tplcache\" class=\"checkbox\" checked /><label for=\"tplcache\">".$lang[tools_updatecache_tpl]."</label><input type=\"checkbox\" name=\"type[]\" value=\"blockclass\" id=\"blockclasscache\" class=\"checkbox\" /><label for=\"blockclasscache\">".$lang[tools_updatecache_blockclass].'</label>', 'action=tools&operation=updatecache&step=2', 'form', '', FALSE);替换为:
showtips('tools_updatecache_tips');4 q0 ~8 J6 T# }0 d
echo '<br>';% L+ Z8 B. o0 U( E* q* E: Z7 @
/ k, ~- G7 c6 |( Y0 H if($step == 1) {
6 t0 z& `! F! o4 z9 N6 A* J4 V: Q if($_G['siteurl'] == $_G['setting'][siteurl]) {
. {- g2 j. v8 z- ?6 r% B cpmsg("<input type=\"checkbox\" name=\"type[]\" value=\"data\" id=\"datacache\" class=\"checkbox\" checked /><label for=\"datacache\">".$lang[tools_updatecache_data]."</label><input type=\"checkbox\" name=\"type[]\" value=\"tpl\" id=\"tplcache\" class=\"checkbox\" checked /><label for=\"tplcache\">".$lang[tools_updatecache_tpl]."</label><input type=\"checkbox\" name=\"type[]\" value=\"blockclass\" id=\"blockclasscache\" class=\"checkbox\" /><label for=\"blockclasscache\">".$lang[tools_updatecache_blockclass].'</label>', 'action=tools&operation=updatecache&step=2', 'form', '', FALSE);( J: ?0 i" {3 b
} else {
- X8 Q8 B- G* I0 m! Q1 M+ G6 @: } cpmsg('请切换到主域名下更新缓存', '', 'succeed', '', FALSE);
五、http:// 跳转至 https://
打开 source/class/class_core.php 文件,在
set_exception_handler(array('core', 'handleException'));后面加入:
if($_SERVER['SERVER_PORT'] != '443' && $_SERVER['PHP_SELF'] != '/api/uc.php') {
5 ~" f5 m1 |2 Z! t5 Y if(!preg_match("/(Zidingyi|Bot|Crawl|Spider|slurp|sohu-search|lycos|robozilla)/i", $_SERVER['HTTP_USER_AGENT'])) {
3 N# h' | I$ O3 t% T; X; n header('HTTP/1.1 301 Moved Permanently');& Z9 }/ C# R& X7 I
header('Location: https://'.$_SERVER['HTTP_HOST'].$_SERVER['REQUEST_URI']);7 q8 U( A2 A# A# m8 p/ `: l
exit; n* l) }, T# ]8 r/ {
} elseif(preg_match("/(Baidu|Google)/i", $_SERVER['HTTP_USER_AGENT'])) {
: K; i6 _# e: X0 T* c header('HTTP/1.1 403 Forbidden');, o8 @- v5 z! l; W2 i
exit;
9 E) `' N$ X% @ U* N7 ]+ |0 e5 ~: O/ l }
0 W. t8 d R0 _7 m9 M}说明:当访问端口不为443(即https)时,如果不是搜索引擎则跳转到https页面,否则如果是百度或Google蜘蛛(这两个搜索引擎已支持收录https)则返回403禁止访问,避免重复收录 http 和 https 或优先收录了 http ,其它搜索引擎未定义,正常返回 http 页面(其它搜索引擎可能不支持收录 https ,因此开放 http 给他们)。
以上代码中“Zidingyi”可以任意修改,管理员使用以下UA可以不跳转到https,便于对http版进行调测:
Mozilla/5.0 (compatible; Zidingyi/2015; +http://www.xxx.com)
六、其它问题
解决 Discuz! X3.* “允许发表的域名列表”中的域名在非http协议下失效的问题
Discuz! X3.* 开启SSL后手机版图片链接替换为https地址
作者: 北美生活网 时间: 2017-4-6 11:55
https://www.digitalocean.com/community/tutorials/how-to-set-up-apache-with-a-free-signed-ssl-certificate-on-a-vps
Note: You may want to consider using Let's Encrypt instead of the StartSSL.com process below. Let's Encrypt is a new certificate authority that provides a free and easy way of creating SSL/TLS certificates that are trusted in most web browsers. Check out the tutorial to get started: How To Secure Apache with Let's Encrypt on Ubuntu 14.04
Prerequisites
Before we get started, here are the web tools you need for this tutorial:
- Google Chrome browser
- Apache installed on your VPS (cloud server)
- A domain name you own
- Access to an email address at that domain, either:
- postmaster@duable.co
- hostmaster@duable.co
- webmaster@duable.co
StartSSL.com offers completely free verified (your users won't have to see those scary red screens saying "this site isn't trusted" anymore) SSL certificates that you can use on your website. This is a great deal as most companies charge $50-$60 for similar services. The free version is a bit tricky to set up, but it's well worth it.
To get started, browse to StartSSL.com and using the toolbar on the left, navigate to StartSSL Products and then to StartSSL™ Free. Choose the link for Control Panel from the top of the page.
Make sure you are using Google Chrome
- Choose the Express Signup. option
- Enter your personal information, and click continue.
- You'll get an email with a verification code inside it shortly. Copy and paste that email into the form on StartSSL's page.
- They will review your request for a certificate and then send you an email with the new info. This process might take as long as 6 hours though, so be patient.
- Once the email comes, use the link provided and the new authentication code (at the bottom of the email) to continue to the next step.
- They will ask you to Generate a private key and you will be provided with the choice of "High" or "Medium" grade. Go ahead and choose "High".
- Once your key is ready, click Install.
- Chrome will show a popdown that says that the certificate has been succesfully installed to Chrome.
This means your browser is now authenticated with your new certificate and you can log into the StartSSL authentication areas using your new certificate. Now, we need to get a properly formatted certificate set up for use on your VPS. Click on the Control panel link again, and choose the Authenticate option. Chrome will show a popup asking if you want to authenticate and will show the certificate you just installed. Go ahead and authenticate with that certificate to enter the control panel.
You will need to validate your domain name to prove that you own the domain you are setting up a certificate for. Click over to the Validations Wizard in the Control panel and set Type to Domain Name Validation. You'll be prompted to choose from an email at your domain, something like [email]postmaster@yourdomain.com[/email].
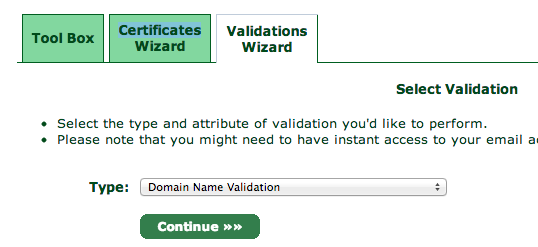
Check the email inbox for the email address you selected. You will get yet another verification email at that address, so like before, copy and paste the verification code into the StartSSL website.
Next, go to the Certificates Wizard tab and choose to create a Web Server SSL/TLS Certificate.
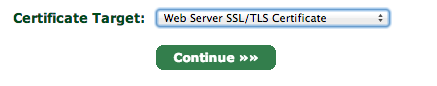
Hit continue and then enter in a secure password, leaving the other settings as is.
You will be shown a textbox that contains your private key. Copy and paste the contents into a text editor and save the data into a file called ssl.key.
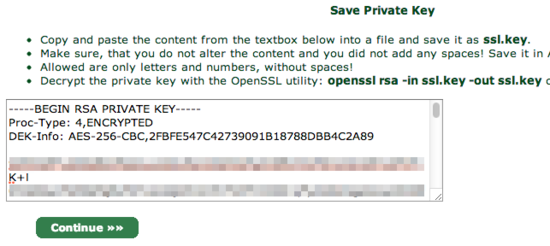
When you click continue, you will be asked which domain you want to create the certificate for:
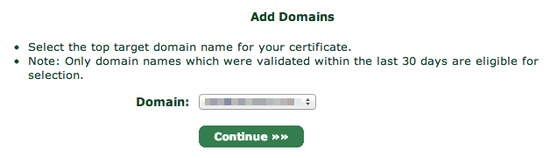
Choose your domain and proceed to the next step.
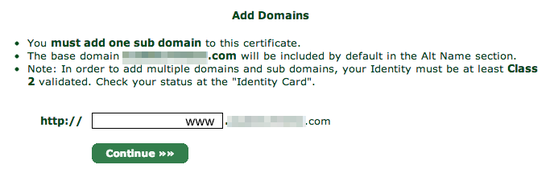
You will be asked what subdomain you want to create a certificate for. In most cases, you want to choose www here, but if you'd like to use a different subdomain with SSL, then enter that here instead:
StartSSL will provide you with your new certificate in a text box, much as it did for the private key:
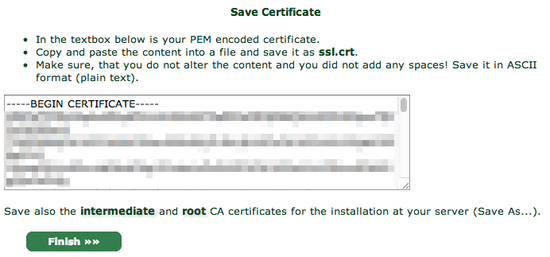
Again, copy and paste into a text editor, this time saving it as ssl.crt.
You will also need the StartCom Root CA and StartSSL's Class 1 Intermediate Server CA in order to authenticate your website though, so for the final step, go over to the Toolbox pane and choose StartCom CA Certificates:

At this screen, right click and Save As two files:
- StartCom Root CA (PEM Encoded) (save to ca.pem)
- Class 1 Intermediate Server CA (save to sub.class1.server.ca.pem)
For security reasons, StartSSL encrypts your private key (the ssl.key file), but your web server needs the unencrypted version of it to handle your site's encryption. To unencrypt it, copy it onto your server, and use the following command to decrypt it into the file private.key:
openssl rsa -in ssl.key -out private.key
OpenSSL will ask you for your password, so enter it in the password you typed in on StartSSL's website.
At this point you should have five files. If you're missing any, double-check the previous steps and re-download them:
- ca.pem - StartSSL's Root certificate
- private.key - The unencrypted version of your private key (be very careful no one else has access to this file!)
- sub.class1.server.ca.pem - The intermediate certificate for StartSSL
- ssl.key - The encrypted version of your private key (does not need to be copied to server)
- ssl.crt - Your new certificate
You can discard the ssl.key file. If you haven't already copied the others onto your server you upload them there now:
scp {ca.pem,private.key,sub.class1.server.ca.pem,ssl.crt} YOURSERVER:~ 2 V& L7 R, G8 ]7 S$ L. Z
Activating the certificate in Apache
Having a certificate isn't any good if you can't actually use it. This section explains how to configure Apache to use your new SSL certificate. These instructions are for Apache running on recent versions of Ubuntu VPS. For other Linux-based distros or web servers, you'll have to adjust accordingly.
First, create the folders where we'll store the keys. Enable Apache's SSL module, and restart Apache.
sudo a2enmod ssl5 g w+ v' c1 V4 |/ ^( j5 d
sudo service apache2 restart
+ a J+ Z; |' r" N! u' Lsudo mkdir -p /etc/apache2/ssl
# T& [0 y& M* n+ O* Z
Copy the files you set up in the previous section into the /etc/apache2/ssl folder on your VPS.
sudo mkdir -p /etc/apache2/ssl, N' P" L4 G9 H1 z: v
cp ~/{ca.pem,private.key,sub.class1.server.ca.pem,ssl.crt} /etc/apache2/ssl
/ a, A' t4 j% @5 s; a! v4 n0 {" WExecute:
ls /etc/apache2/ssl
And it should return:
ca.pem
" H. Y" f9 z! R% x$ L/ Tssl.crt; {% L+ F- X9 Z& Y& E
private.key2 e' m2 w3 O$ ]7 t
sub.class1.server.ca.pemNow, open your apache2 configuration file. Unless you've already modified the default configuration, input:
nano /etc/apache2/sites-enabled/000-default
It should look something like this:
<VirtualHost *:80>
1 b5 ^3 [' s# Q& a ServerAdmin webmaster@localhost
0 F' X. Y! v' K3 Z9 u' b
4 l/ e% l- X# J- P: ~% w" `0 `, \ DocumentRoot /var/www
* {* h1 i% Y/ g, L" B% P <Directory />
2 S* K/ F: `) [. p4 q Options FollowSymLinks
2 N/ g$ X v/ c) ?. M( R5 X; { AllowOverride None
3 }/ o, f( n1 `6 n' A& w2 N$ v6 R </Directory>, M k' x) Q" n( g: s1 D$ B
<Directory /var/www/>& M* {+ J! u: k5 |- o9 |* _& {
Options Indexes FollowSymLinks MultiViews
6 n9 |7 U4 E2 o3 h+ m AllowOverride None! O2 e& s( w2 ~- [/ E
Order allow,deny. l, X/ G+ s' i. O$ V
allow from all
$ {) Q6 Q) w2 E% N8 S </Directory>9 A9 i) a4 N- T/ y# Q/ g6 f
3 A! I8 a7 ~9 L2 J' b4 p8 w8 {. {
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/1 l( O' Y( \/ V
<Directory "/usr/lib/cgi-bin">0 y* s1 @% M# m
AllowOverride None
) C$ i; L, h- J; h9 ?4 d# t( O Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch Z% n8 y! u8 L: Z
Order allow,deny
6 P/ f0 K7 X" O# I6 V r Allow from all% E* d4 P- H; v# l: i3 e
</Directory>$ L* }3 b( S) l+ w2 h7 ]1 \
% j2 }& f7 x1 ~! N# V0 d2 z7 ~ ErrorLog ${APACHE_LOG_DIR}/error.log5 K9 h3 d& O2 X5 L
9 d/ i w( y* G5 I4 j: P
# Possible values include: debug, info, notice, warn, error, crit,1 ? q, T' C1 K
# alert, emerg.7 H0 M. E' v5 v* b- e' V, l
LogLevel warn
/ A @7 M9 f, _( O3 ?8 x$ W1 v. h" V+ B$ }4 Z8 |% n
CustomLog ${APACHE_LOG_DIR}/access.log combined
4 ^$ z: f0 J0 b, z
) x# Y0 y' i: H. f( ~$ S# Z) k: h Alias /doc/ "/usr/share/doc/") A" b: {, z7 I9 ~& G! J6 F
<Directory "/usr/share/doc/">0 e& L6 [- \6 L6 ^# x* w
Options Indexes MultiViews FollowSymLinks
) r) Z/ \1 w; l! B9 g& {- H AllowOverride None7 s: z* @" V8 U
Order deny,allow, w0 [2 E4 k4 Q* E: V# }
Deny from all4 v8 g6 f" \3 W ^) ^ }* d# o
Allow from 127.0.0.0/255.0.0.0 ::1/128
6 F9 J W% l! r+ n2 @% @! x; _ L </Directory>: a' j5 F7 y# i
7 U/ I) x: a, Y; r7 @& F</VirtualHost>
9 s* E9 Q0 ?; k) ICopy the entire script above (from <VirtualHost *:80> to </VirtualHost>), paste it below the existing one, and change the top line from:
<VirtualHost *:80>
to
<VirtualHost *:443>
And add the following lines after the <VirtualHost *:443> line:
SSLEngine on ' s% y& y* U( S6 {0 ]) H
SSLProtocol all -SSLv2 0 m3 @ e! q: [) {
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM 5 C$ u. }' a& l7 }! z& W
) s4 h# \7 e) ~4 R* b- A+ C% M6 N# c4 LSSLCertificateFile /etc/apache2/ssl/ssl.crt . c6 D$ G; N& a+ M$ e0 f8 E" z
SSLCertificateKeyFile /etc/apache2/ssl/private.key ) d* r& [ [8 F! Z
SSLCertificateChainFile /etc/apache2/ssl/sub.class1.server.ca.pem The end result should look like this:
<VirtualHost *:80>
2 w+ p2 ]' w2 V z9 o ServerAdmin webmaster@localhost4 H& Z; ^! `/ T( C5 O' b5 C
* {+ c9 v% \+ I6 M2 y DocumentRoot /var/www! D4 g$ k+ m+ j$ D* |7 G) T
<Directory />8 G5 r$ B Y3 |0 I
Options FollowSymLinks
& g, s! N+ L' x0 `1 l AllowOverride None: \+ X* W( y- \) O) o5 d
</Directory>6 I$ J5 R8 b9 E+ S& K! x* \! L
<Directory /var/www/>
7 v: h, s, {; z% O' _1 U Options Indexes FollowSymLinks MultiViews$ |+ P4 \' _( x% C- [
AllowOverride None
# S% M2 a" r, O. t/ P4 E Order allow,deny& k& o7 k8 J# ?9 S; e$ p( U- W
allow from all
& f9 i k4 N5 c# f+ _7 I, _ </Directory>0 C( q: z: L2 o2 y9 p" R3 p# d$ a
) m% P. F b2 I* b) x ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
: C" @) ]: L7 [/ p% i9 D: ^ <Directory "/usr/lib/cgi-bin">
) t0 z: {6 i$ i& g8 f AllowOverride None% g9 J( A% [9 S+ N! V; n! R
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
/ ] T7 d' C( ]4 p* C0 [) V/ m Order allow,deny
% l+ S3 b3 v5 ~" m! h- m% [ Allow from all
# ?/ ?& p" }- \& `3 D" P </Directory>9 K* s$ Y- u! s* w2 o* E" y4 J( y
( ~2 M! H5 i# B% w2 V
ErrorLog ${APACHE_LOG_DIR}/error.log
# G2 V1 f/ F' d* Y
' |, @. Z1 S% n1 H # Possible values include: debug, info, notice, warn, error, crit,
: {" P0 g7 u! r' n8 t6 i" f& A # alert, emerg.
) {( V( z/ M: d6 D6 K5 S' s0 Q LogLevel warn8 x5 ]1 n! S t' P& r0 l5 V
- ]+ z- z. w; N
CustomLog ${APACHE_LOG_DIR}/access.log combined% X% J4 N& i( T. ~3 L2 y3 B3 _% }1 X4 I
- N# j- `! b3 v" l/ e
Alias /doc/ "/usr/share/doc/"
% |5 j0 }/ l3 ?! o$ z$ a <Directory "/usr/share/doc/">
* \! j1 ^# O& t+ ~( T0 D4 B' O Options Indexes MultiViews FollowSymLinks
8 O( E, s+ k. _( h( ~* ] AllowOverride None+ A; m- Y, }0 x3 w
Order deny,allow
7 l& p R) d3 b7 o Deny from all
( L# m7 P$ h/ m5 ^1 |5 g/ ` Allow from 127.0.0.0/255.0.0.0 ::1/128: ^4 b6 b; ^$ g3 f/ g: w
</Directory> {) o5 V% a+ f; Y
* F! j2 g5 h; d: p" ~7 B6 h" E4 w: {
</VirtualHost>
" E2 Q+ J8 W4 F" W' H" T& c
* P5 I" e2 J, T+ L" G) Z<VirtualHost *:443>5 Z. x5 z6 ^4 z! K% r- G
SSLEngine on - W+ ?% S/ P' U9 G. R' l* i
SSLProtocol all -SSLv2 # Z/ J' S% o9 i, p$ m
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM - z% S$ G$ _( g3 ?
5 U9 ^ d7 R; `. ?# @' ~) _9 G SSLCertificateFile /etc/apache2/ssl/ssl.crt
) \( d$ v. w8 ], U; h SSLCertificateKeyFile /etc/apache2/ssl/private.key
9 h4 O2 n0 m5 N$ W. t& N SSLCertificateChainFile /etc/apache2/ssl/sub.class1.server.ca.pem
% P- ]% [( A1 Z9 k, K* m, R5 z ServerAdmin webmaster@localhost
F- P% X5 \: a8 k5 j+ Z! m- \6 z8 D9 p
: H. N" h, |7 F6 k0 x8 ] DocumentRoot /var/www
- A" M1 C! [% d& u2 Y. H7 v <Directory />
5 E5 [5 Q: ^. K. _ Options FollowSymLinks+ A3 y( [8 h( a- }; Q
AllowOverride None. E0 t2 O, `- E( e4 P2 S! ?* U
</Directory>
( R$ j9 g# q6 ~. l4 N; F! f <Directory /var/www/>1 z d: ?7 A( J* K( y* U- c
Options Indexes FollowSymLinks MultiViews2 H4 F5 x' f2 r. V+ c2 Y- z4 ^# X
AllowOverride None$ [- s9 z2 z% L6 [1 k/ \
Order allow,deny! K* Z5 `( F H% m: x5 U
allow from all9 e7 o+ _. D; b0 x
</Directory>
7 a: ^2 v6 l& s$ \8 i2 X2 {+ _2 s$ l
0 l- ]8 j$ P& W2 g& r ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/! S+ R6 V/ i; T$ n9 b6 O* f
<Directory "/usr/lib/cgi-bin">/ ]# ^8 H; Z% b% ]1 S& j
AllowOverride None
) }* Z: a F: j* y2 o$ q0 [ Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
7 f5 I: g, C9 D$ H& t: k Order allow,deny. n' c4 O* K! `
Allow from all' {( `" o, @& {, o* K
</Directory>' J4 V8 `$ z2 O
/ K* z0 L/ C1 g+ Z ErrorLog ${APACHE_LOG_DIR}/error.log
% K! N- b9 M: h: t2 J7 z* f" t3 K6 V
# Possible values include: debug, info, notice, warn, error, crit,! {9 m- ^6 k7 f# j! i
# alert, emerg.. k0 G9 f" V, s
LogLevel warn& o1 B# m H8 j$ Y! `5 |: `' M
( H' A% j6 J2 s1 l5 `; e CustomLog ${APACHE_LOG_DIR}/access.log combined
) c. z- n8 {3 t, Y5 e G# |# r
. b8 s4 `& W* Q6 J Alias /doc/ "/usr/share/doc/"6 Y2 A9 Q9 M5 X8 j
<Directory "/usr/share/doc/">
: e! {. m" R3 n5 i5 P$ z& x1 C" ` Options Indexes MultiViews FollowSymLinks ^6 b! m [6 j1 q' e$ S7 ^1 V2 X* A
AllowOverride None6 k, i7 \. L( f, | i
Order deny,allow3 D% V9 M; u3 p9 S4 H8 L% `
Deny from all
r" | u! _" b( { Allow from 127.0.0.0/255.0.0.0 ::1/128
: X+ ]: `0 q- _) Z8 [$ e </Directory>* q8 P1 ]$ I6 g5 P; m
2 G t6 }; i. R; I% L</VirtualHost>Save your files and restart Apache with:
sudo service apache2 restart
You can check Apache's log files to see if there are any show stopping errors with this command:
cat /var/log/apache2/error.log0 x" k$ j4 J+ E* ~4 Q+ o/ d3 G
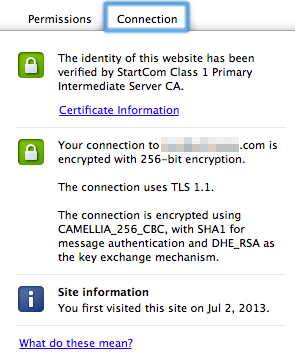
If everything looks good, try accessing your site in your web browser using an HTTPS URL (e.g. https://www.YOURSITE.com). When your site loads, you should see a little green padlock icon next to the URL. Click on it and you should see the following. The connections tab should show that the site's identity has been verified by StartCom.
Congratulations! You are all set!
Reference Links:
Here are some of the other posts I consulted when putting this together. If you run into any problems they might be a source of inspiration on how to fix them:
作者: 北美生活网 时间: 2017-4-6 12:02
How To Secure Apache with Let's Encrypt on Ubuntu 14.04https://www.digitalocean.com/community/tutorials/how-to-secure-apache-with-let-s-encrypt-on-ubuntu-14-049 T5 t4 k. Y6 j4 \. W. f0 c
# P. r7 r& S! A* _/ Q. k* ]
) K7 z4 ?; X( ]- \IntroductionThis tutorial will show you how to set up a TLS/SSL certificate from https://letsencrypt.org/ on an Ubuntu 14.04 server running Apache as a web server. We will also cover how to automate the certificate renewal process using a cron job.
SSL certificates are used within web servers to encrypt the traffic between the server and client, providing extra security for users accessing your application. Let’s Encrypt provides an easy way to obtain and install trusted certificates for free.
* \' J1 Z0 ] e7 z: N8 B
PrerequisitesIn order to complete this guide, you will need:
- An Ubuntu 14.04 server with a non-root sudo user, which you can set up by following our https://www.digitalocean.com/community/tutorials/initial-server-setup-with-ubuntu-14-04 guide
- The Apache web server installed with https://www.digitalocean.com/community/tutorials/how-to-set-up-apache-virtual-hosts-on-ubuntu-14-04-lts properly configured- b% h- z$ M& V% V: q* H
When you are ready to move on, log into your server using your sudo account.
* p( c: Y" o6 d+ K+ ~! {4 H1 ?# _' ]
Step 1 — Download the Let’s Encrypt ClientFirst, we will download the certbot-auto Let’s Encrypt client from the EFF download site. The client will automatically pull down available updates as necessary after installation.
We can download the certbot-auto Let’s Encrypt client to the /usr/local/sbin directory by typing:
- cd /usr/local/sbin
- sudo wget https://dl.eff.org/certbot-auto0 c, W) T- f- B) _; @! F( K
You should now have a copy of certbot-auto in the /usr/local/sbin directory.
Make the script executable by typing:
- sudo chmod a+x /usr/local/sbin/certbot-auto( J- c1 v! p4 u! U
The certbot-auto client should now be ready to use.
5 ]; r1 t1 v4 `6 j
Step 2 — Set Up the SSL CertificateGenerating the SSL Certificate for Apache using the certbot-auto Let’s Encrypt client is quite straightforward. The client will automatically obtain and install a new SSL certificate that is valid for the domains provided as parameters.
To execute the interactive installation and obtain a certificate that covers only a single domain, run the certbot-auto command with:
- certbot-auto --apache -d example.com9 m$ D2 P+ b1 F* X+ X% f' K
If you want to install a single certificate that is valid for multiple domains or subdomains, you can pass them as additional parameters to the command. The first domain name in the list of parameters will be the base domain used by Let’s Encrypt to create the certificate, and for that reason we recommend that you pass the bare top-level domain name as first in the list, followed by any additional subdomains or aliases:
- certbot-auto --apache -d example.com -d www.example.com
0 I+ j0 Q0 M6 e" Y! C! Q
For this example, the base domain will be example.com.
After the dependencies are installed, you will be presented with a step-by-step guide to customize your certificate options. You will be asked to provide an email address for lost key recovery and notices, and you will be able to choose between enabling both http and https access or force all requests to redirect to https.
When the installation is finished, you should be able to find the generated certificate files at /etc/letsencrypt/live. You can verify the status of your SSL certificate with the following link (don’t forget to replace example.com with your base domain):
https://www.ssllabs.com/ssltest/analyze.html?d=example.com&latestYou should now be able to access your website using a https prefix.
[ @' b, R6 t# d, n* H1 E
Step 3 — Set Up Auto RenewalLet’s Encrypt certificates are valid for 90 days, but it’s recommended that you renew the certificates every 60 days to allow a margin of error. The certbot-auto Let's Encrypt client has a renew command that automatically checks the currently installed certificates and tries to renew them if they are less than 30 days away from the expiration date.
To trigger the renewal process for all installed domains, you should run:
certbot-auto renewBecause we recently installed the certificate, the command will only check for the expiration date and print a message informing that the certificate is not due to renewal yet. The output should look similar to this:
Checking for new version...Requesting root privileges to run letsencrypt... /home/sammy/.local/share/letsencrypt/bin/letsencrypt renewProcessing /etc/letsencrypt/renewal/example.com.confThe following certs are not due for renewal yet: /etc/letsencrypt/live/example.com/fullchain.pem (skipped)No renewals were attempted.Notice that if you created a bundled certificate with multiple domains, only the base domain name will be shown in the output, but the renewal should be valid for all domains included in this certificate.
A practical way to ensure your certificates won’t get outdated is to create a cron job that will periodically execute the automatic renewal command for you. Since the renewal first checks for the expiration date and only executes the renewal if the certificate is less than 30 days away from expiration, it is safe to create a cron job that runs every week or even every day, for instance.
Let's edit the crontab to create a new job that will run the renewal command every week. To edit the crontab for the root user, run:
- sudo crontab -e4 H1 A/ c' k1 b: ~
Include the following content, all in one line:
[color=rgba(0, 0, 0, 0.298039)]crontab( Z6 p& ?+ S& M0 C- ]' t
30 2 * * 1 /usr/local/sbin/certbot-auto renew >> /var/log/le-renew.logSave and exit. This will create a new cron job that will execute the letsencrypt-auto renew command every Monday at 2:30 am. The output produced by the command will be piped to a log file located at /var/log/le-renewal.log.
For more information on how to create and schedule cron jobs, you can check our https://www.digitalocean.com/community/tutorials/how-to-use-cron-to-automate-tasks-on-a-vps guide.
- i' }- D5 q4 Z5 p
- F) G& \& O- ]' o. D* ~& w
作者: 北美生活网 时间: 2017-4-6 12:06
How To Use Cron To Automate Tasks On a VPS1 z" A' k( m5 ?' b9 U/ Y, ?
https://www.digitalocean.com/community/tutorials/how-to-use-cron-to-automate-tasks-on-a-vps
1 ~6 D1 ~7 J K' F: T# G/ k. Z3 s5 ?& N
/ b' O/ T% U: a9 f/ fIntroductionOne of the most standard ways to run tasks in the background on Linux machines is with cron jobs. They’re useful for scheduling tasks on the VPS and automating different maintenance-related jobs. “Cron” itself is a daemon (or program) that runs in the background. The schedule for the different jobs that are run is in a configuration file called “crontab.”
! Y* N- O( k$ W' l' }InstallationAlmost all distros have a form of cron installed by default. However, if you’re using a system that doesn’t have it installed, you can install it with the following commands:
For Ubuntu/Debian:
sudo apt-get updatesudo apt-get install cronFor Cent OS/Red Hat Linux:
sudo yum updatesudo yum install vixie-cron crontabsYou’ll need to make sure it runs in the background too:
sudo /sbin/chkconfig crond onsudo /sbin/service crond start8 L" W0 K5 Z6 w% ?
SyntaxHere is an example task we want to have run:
5 * * * * curl http://www.google.comThe syntax for the different jobs we’re going to place in the crontab might look intimidating. It’s actually a very succinct and easy-to-parse if you know how to read it. Every command is broken down into:
- Schedule
- Command
% f2 Y7 t: D& Y" H a' N2 a
The command can be virtually any command you would normally run on the command line. The schedule component of the syntax is broken down into 5 different options for scheduling in the following order:
- minute
- hour
- day of the month
- month
- day of the week
- b- i1 z1 T Q: Z
. g3 |3 @1 ^" ^9 J, w% U
ExamplesHere is a list of examples for some common schedules you might encounter while configuring cron.
To run a command every minute:
* * * * *To run a command every 12th minute on the hour:
12 * * * *You can also use different options for each placeholder. To run a command every 15 minutes:
0,15,30,45 * * * *To run a command every day at 4:00am, you’d use:
0 4 * * *To run a command every Tuesday at 4:00am, you’d use:
0 4 * * 2You can use division in your schedule. Instead of listing out 0,15,30,45, you could also use the following:
*/4 2-6 * * *Notice the “2-6” range. This syntax will run the command between the hours of 2:00am and 6:00am.
The scheduling syntax is incredibly powerful and flexible. You can express just about every possible time imaginable.
6 ?) H& [% @6 ? U, A
ConfigurationOnce you’ve settled on a schedule and you know the job you want to run, you’ll have to have a place to put it so your daemon will be able to read it. There are a few different places, but the most common is the user’s crontab. If you’ll recall, this is a file that holds the schedule of jobs cron will run. The files for each user are located at /var/spool/cron/crontab, but they are not supposed to be edited directly. Instead, it's best to use the crontab command.
You can edit your crontab with the following command:
crontab -eThis will bring up a text editor where you can input your schedule with each job on a new line.
If you’d like to view your crontab, but not edit it, you can use the following command:
crontab -lYou can erase your crontab with the following command:
crontab -rIf you’re a privileged user, you can edit another user’s by specifying crontab -u <user> -e
. U1 m7 L# D3 M) Y% r% K
OutputFor every cron job that gets executed, the user’s email address that’s associated with that user will get emailed the output unless it is directed into a log file or into /dev/null. The email address can be manually specified if you provide a “MAILTO” setting at the top of the crontab. You can also specify the shell you’d like run, the path where to search for the cron binary and the home directory with the following example:
First, let’s edit the crontab:
crontab -eThen, we’ll edit it like so:
SHELL=/bin/bashHOME=/MAILTO=”[email]example@digitalocean.com[/email]”#This is a comment* * * * * echo ‘Run this command every minute’This particular job will output "Run this command every minute." That output will get emailed every minute to the “mailto:example@digitalocean.com” email address I specified. Obviously, that might not be an ideal situation. As mentioned, we can also pipe the output into a log file or into an empty location to prevent getting an email with the output.
To append to a log file, it’s as simple as:
* * * * * echo ‘Run this command every minute’ >> file.logNote: “>>” appends to a file.
If you want to pipe into an empty location, use /dev/null. Here is a PHP script that gets executed and runs in the background.
* * * * * /usr/bin/php /var/www/domain.com/backup.php > /dev/null 2>&1& E5 [9 x' v: G9 G5 \# i0 y/ R6 Q
Restricting AccessRestricting access to cron is easy with the /etc/cron.allow and /etc/cron.deny files. In order to allow or deny a user, you just need to place their username in one of these files, depending on the access required. By default, most cron daemons will assume all users have access to cron unless one of these file exists. To deny access to all users and give access to the user tdurden, you would use the following command sequence:
echo ALL >>/etc/cron.denyecho tdurden >>/etc/cron.allowFirst, we lock out all users by appending "ALL" to the deny file. Then, by appending the username to the allow file, we give the user access to execute cron jobs.
+ R4 l/ ?& w; o) U5 z$ ^- g# WSpecial SyntaxThere are several shorthand commands you can use in your crontab file to make administering a little easier. They are essential shortcuts for the equivalent numeric schedule specified:
- @hourly - Shorthand for 0 * * * *
- @daily - Shorthand for 0 0 * * *
- @weekly - Shorthand for 0 0 * * 0
- @monthly - Shorthand for 0 0 1 * *
- @yearly - Shorthand for 0 0 1 1 *
3 ~& _" I0 y8 U* J
and @reboot, which runs the command once at startup.
Note: Not all cron daemons can parse this syntax (particularly older versions), so double-check it works before you rely on it.
To have a job that runs on start up, you would edit your crontab file (crontab -e) and place a line in the file similar to the following:
@reboot echo "System start up"This particular command would get executed and then emailed out to the user specified in the crontab.
8 x0 y! z" e+ a4 M8 P/ }7 p- O
: j( I4 e% d) E1 l7 |8 @9 f( _
作者: 北美生活网 时间: 2017-4-6 12:10
https://debian-administration.org/article/349/Setting_up_an_SSL_server_with_Apache28 n1 T* C+ M, M2 ?$ C
, `: R" L M4 `Setting up an SSL server with Apache2
: c/ h- j+ Z- p1 c+ t1 s; W# m/ R- z& W' s8 Z
With the introduction of the Apache2 packages in Debian it is much simpler to create and use a secure SSL protected webserver than in the old days http://www.debian-administration.org/articles/31, here we'll show how it is done.
If you have Apache 2.x installed already then you're good to go as you don't need anything extra installed.
If you haven't got it installed then you can do so easily:
earth:~# apt-get install apache2Reading Package Lists... DoneBuilding Dependency Tree... DoneThe following extra packages will be installed: apache2-common apache2-mpm-worker apache2-utils openssl ssl-certSuggested packages: apache2-doc ca-certificatesThe following NEW packages will be installed: apache2 apache2-common apache2-mpm-worker apache2-utils openssl ssl-cert0 upgraded, 6 newly installed, 0 to remove and 0 not upgraded.Need to get 2040kB of archives.After unpacking 6218kB of additional disk space will be used.Do you want to continue? [Y/n]Once the server is installed you need to do three things to get a working SSL setup:
- Generate, or import, a certificate.
- Enable Apaches SSL support.
- Configure your SSL options.( [2 m& L& H+ D* g/ T' p9 q: ~3 p
Generating A Certificate
Generating a certificate from scratch will give you something which will be used to protect the traffic exchanged between clients and your server, however it will be signed by a untrusted certificate authority so it will generate warnings.
Importing a paid and "trusted" certificate will avoid this problem, but that is beyond the scope of this simple introduction.
Generating an SSL certificate for Apache2 may be accomplished using the apache2-ssl-certificate script. This will ask you questions interactively then generate the certificate file appropriately.
Here's a sample session:
earth:~# apache2-ssl-certificatecreating selfsigned certificatereplace it with one signed by a certification authority (CA)enter your ServerName at the Common Name promptIf you want your certificate to expire after x days call this programmwith -days xGenerating a 1024 bit RSA private key............++++++..........................++++++writing new private key to '/etc/apache2/ssl/apache.pem'-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [GB]:State or Province Name (full name) [Some-State]:ScotlandLocality Name (eg, city) []:EdinburghOrganization Name (eg, company; recommended) []:Steve KempOrganizational Unit Name (eg, section) []:server name (eg. ssl.domain.tld; required!!!) []:earthEmail Address []: [email]earth-admin@steve.org.uk[/email]Enabling SSL Support
To use the SSL facilities of Apache2 you must enable the module mod_ssl, this can be achieved using the helper tool a2enmod (We've previously http://www.debian-administration.org/articles/207.)
As root run:
earth:~# a2enmod sslModule ssl installed; run /etc/init.d/apache2 force-reload to enable.Once this is done you'll have Apache setup to accept SSL connections, but the server will still only be listening for incoming HTTP requests on port 80 - and not SSL connections on port 443. To fix this you must add a line to the file /etc/apache2/ports.conf:
Listen 443With these two steps out of the way you now have an Apache setup which will listen for and accept SSL connections. The next step is to modify your virtualhosts to use it.
Configuring your SSL Hosts
With a certificate setup, and the server updated to load and listen for incoming SSL connections you're almost finished. The final step is to ensure that your virtual hosts, or main host, will accept SSL options.
I use virtual hosts upon my machine and this just means adding a couple of options to each one I wish to use SSL:
SSLEngine onSSLCertificateFile /etc/apache2/ssl/apache.pemFor reference here is a complete example which should be easy to modify/understand:
NameVirtualHost *:443NameVirtualHost *:80<VirtualHost *:80> ServerName earth.my.flat DocumentRoot /var/www/ ErrorLog /var/log/apache2/error.log CustomLog /var/log/apache2/access.log combined</VirtualHost><VirtualHost *:443> ServerName earth.my.flat DocumentRoot /var/www/ ErrorLog /var/log/apache2/error.log CustomLog /var/log/apache2/access.log combined SSLEngine on SSLCertificateFile /etc/apache2/ssl/apache.pem</VirtualHost>
8 Z% ~# y) \$ S5 i6 B( U
作者: 北美生活网 时间: 2017-4-6 12:12
Redirect HTTP to HTTPS automatically1 k2 M0 a1 [6 f' ^, ~2 l
https://ca.godaddy.com/help/redirect-http-to-https-automatically-8828: \% d4 N' h% Z
. L# z+ }3 ], w% f5 Z1 [
- A8 u: X% Y8 v4 F, O8 Z5 bIf you have a secure certificate (SSL) on your website, you can automatically redirect visitors to the secured (HTTPS) version of your website to make sure their information is protected.
How you redirect traffic depends on https://ca.godaddy.com/help/what-type-of-hosting-account-do-i-have-6971.
Linux & cPanelLinux-based accounts use .htaccess files to handle redirection.
If you need to create a .htaccess file, you can use your control panel's file manager (https://ca.godaddy.com/help/managing-your-hosting-accounts-files-12426 / https://ca.godaddy.com/help/create-files-16278).
Using the following code in your .htaccess file automatically redirects visitors to the HTTPS version of your site:
RewriteEngine OnRewriteCond %{HTTPS} offRewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]If you have an existing .htaccess file:
- Do not duplicate RewriteEngine On.
- Make sure the lines beginning RewriteCond and RewriteRule immediately follow the already-existing RewriteEngine On.; Z$ @( A, i* K
Windows & PleskWindows-based accounts use web.config files to handle redirection.
If you need to create a web.config file, you can use your control panel's file manager (https://ca.godaddy.com/help/managing-your-hosting-accounts-files-12426 / https://ca.godaddy.com/help/create-files-16279).
Using the following code in your web.config file automatically redirects visitors to the HTTPS version of your site:
<configuration><system.webServer><rewrite> <rules> <rule name="HTTP to HTTPS redirect" stopProcessing="true"> <match url="(.*)" /> <conditions> <add input="{HTTPS}" pattern="off" ignoreCase="true" /> </conditions> <action type="Redirect" redirectType="Permanent" url="https://{HTTP_HOST}/{R:1}" /></rule> </rules></rewrite></system.webServer></configuration>If you have an existing web.config file:
4 `2 f+ r: m% o4 P. q6 e7 O$ i
& ~( s: G6 \$ D9 Y, s2 }
作者: admin 时间: 2017-4-6 14:51
DISCUZ x3.2 开启301强制跳转https后 门户栏目出现302死循环
' R5 K# ], F' F
: o( |2 T+ d3 ^& H; Q" C3 q! [$ ]) o( m6 K9 } {7 K- N1 h$ @
自己测试figureed out:4 c7 g# M7 N7 d( L A
0 m2 g2 G. }; r& b2 a/ t0 s* Z
1:全局---域名设置---应用域名---全部清除6 M7 ?# J9 N. c# n0 D
U1 }9 {( z; ?* q5 y/ n% _4 E
2:全局---域名设置----根域名设置---频道---留空
/ k6 t" C3 w7 q. T3 E' g9 ~# M. k
. J+ p' f# l* s$ I* Q3 T% g9 ]0 f. h& @
也可参考:
! V9 o* G# L$ k; l$ o8 L1 t6 ^: V, _# T( X9 B1 V! d
DISCUZ x3.2 开启301强制跳转https后 门户栏目出现302死循环
# ]( M+ E S& B* Q) A0 h9 g$ Z \; O' u8 i1 ?. I% w
http://bbs.zhanzhang.baidu.com/thread-166634-1-1.html: J2 X9 e/ ]. e0 d- i/ e& _8 `
+ ^& |+ z$ [ U& @- `' h
4 G0 y9 D/ R: B/ R) Z8 K; _5 Q7 C此方法并不能彻底解决此问题,正确解决方案:
* E! o0 K' M' X$ |% Q% g+ f2 A: A& h- F
用最新版DiscuzX3.3的方法移植3.2上面即可解决
% @1 m6 a; U" x, c7 w# R7 U# c打开
) D% H- j" T5 R7 ]1 h6 Psource/function/cache/cache_portalcategory.php$ ~* g' w' }! f9 Q" d7 U3 p6 N
查找2 l; F& C: H9 n9 D; t+ D# H- E- r
- $portaldomain = 'http://'.$domain['app']['portal'].$_G['siteroot'];
: n% L8 |/ n3 i- d
2 x- z* n0 v0 g0 g' o
[color=rgb(51, 102, 153) !important]复制代码
8 k3 K, M' |# W3 o( O2 m! l& A9 u替换为! `, ~" T! b# O' t" l
- $portaldomain = $_G['scheme'].'://'.$domain['app']['portal'].$_G['siteroot'];
: j+ M4 {4 R P1 F: s+ m. w8 o
' X7 u w* o$ C1 b4 N: w+ k0 S/ U[color=rgb(51, 102, 153) !important]复制代码& O+ r- f# o" A$ z% |3 p
, I8 C Z. a g5 M
# m1 h+ x& s R1 }+ G1 @查找) Q% V0 h3 C) L: n* K
- $portaldomain = 'http://'.$domain['app']['default'].$_G['siteroot'];
, z- m' \) s$ M
# l5 S+ W, U/ ^+ Q2 w[color=rgb(51, 102, 153) !important]复制代码2 _2 X$ Q. z8 g: A' n4 s
替换为$ N4 u" F- v- d% x: S: x0 r% s7 c
- $portaldomain = $_G['scheme'].'://'.$domain['app']['default'].$_G['siteroot'];* Q6 ]7 Z5 E+ n. s: I! K2 r
) j* w$ r8 n2 k- A
[color=rgb(51, 102, 153) !important]复制代码
/ N: C# h7 c" B) ^* U6 p/ F
8 n; I4 [) {6 R" c4 l
( g, h1 h/ |8 p. m查找- A9 K) `6 s+ f9 m/ W- j
- $url = 'http://'.$data[$topid]['domain'].'.'.$channelrootdomain.'/';
4 A5 N0 v. ]" ~0 `
' V! E0 V+ G' [# {) k
[color=rgb(51, 102, 153) !important]复制代码! a* S0 u, V9 a5 |+ T, c' H
替换为
3 N+ A% T) ^8 w8 y/ Z; s0 [! J& O- $url = $_G['scheme'].'://'.$data[$topid]['domain'].'.'.$channelrootdomain.'/';# b" Z0 C/ o8 o0 E
9 }; Y6 h* V# ?. S
[color=rgb(51, 102, 153) !important]复制代码
' G$ W2 J6 N) _1 N
, y3 ~. ]3 i6 E9 Z3 g3 @
5 f, {- J: ~" ^6 y6 {. _3 C% o关于楼主的步骤二的一个特殊解决方案:
* S# D9 H: W0 S9 b; y打开) A% ? ]' y9 a/ q9 M
source/admincp/admincp_domain.php6 _8 Q M6 M# w5 |9 K
删除或者注释此段代码- if(!empty($domain) && in_array($domain, $_G['setting']['domain']['app'])) {
- cpmsg('setting_domain_repeat_error', '', 'error');
- }" ~/ x' }9 M% { }$ K N+ ]) V/ k
9 }/ B8 A6 R3 p[color=rgb(51, 102, 153) !important]复制代码$ y8 j8 b* B$ K" L1 l' L2 D
, p. M) R/ `$ M$ r0 h
此修改是去除“配置中存在重复的域名”检测
+ v1 n+ |! g. ?+ B. d然后在后台——全局——域名设置
4 V* G9 F/ K4 G# G" P7 z. r把首页和默认设置成同样的域名即可
6 V2 k" T( x8 e/ R) j此方法仅限于门户为首页时可去除 portal.php 包括导航栏中的 portal.php+ y4 ~- r7 [5 q& \
& l7 s5 q% q" Q& @- s' D
\template\模板文件夹\portal\
) E4 u# r* e) g3 H) y9 R( z6 O; b& E1 @
list_xxxx.htm (这对应频道文章列表页面中首页对应的链接) 4 i$ b8 x/ P+ q. i
view_xxxxx.htm(这对应文章页面包屑中首页对应的链接)
3 ^% z6 P# {+ B0 y( @$ |- U2 S1 Y6 f! C
把所有在<a href= 也就是有关于输出链接里的9 Z1 _$ p5 Z; O0 u$ w8 { Z5 X" U8 J
- {lang portal}+ k; w3 N+ v4 T* ^+ o* D! M
) k+ V; N" \. b9 }- D
[color=rgb(51, 102, 153) !important]复制代码& d/ ]* @3 Z/ |3 @# L
改为$ c* p* ?4 o( P" c- x$ b* v1 k
7 D9 x8 V- e. b, e) o[color=rgb(51, 102, 153) !important]复制代码% J& A" W9 d8 i) ~! s, H
即可* b" q4 ?% a* @1 `/ Y2 ^5 H% b8 M
' I6 q5 ]1 h& v% Z7 m
后台更新缓冲即可解决!7 y% Q) B/ Y; n) u7 ~
作者: 北美生活网 时间: 2017-4-14 20:41
解决:7 i0 ~% ]4 U! Y
<IfModule mod_headers.c> ' W: _7 D: j7 o* b& c0 q
Header set X-XSS-Protection "1; mode=block" 6 j- z3 d4 Z4 M: Z# w* Z
</IfModule># V' K) \/ [1 q4 o7 ~
% B$ H/ Q, W2 o: A' f2 L/ L
https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-XSS-Protection
4 K; q4 K5 n- d0 r; q/ K% A1 T1 R5 o
<IfModule mod_headers.c>
6 O# f2 C! {# p: ~+ P Header set X-XSS-Protection "0"
9 s( J7 J9 D( N" ~" Y, u0 ]</IfModule>; a" C9 v/ ?5 U1 e9 ?% x
* b5 x$ z; G4 b. M' D* f, o5 g1 G) W/ D: v+ M
将博客文章推荐出现,chrome --X-XSS-Protection
作者: 北美生活网 时间: 2017-4-14 20:43
This page isn’t working
t/ l& q3 _# b* b! Y- E$ x. X
8 Y; o' F- W4 R9 g- C% k/ FChrome detected unusual code on this page and blocked it to protect your personal information (for example, passwords, phone numbers, and credit cards). [; q1 b1 P6 I/ x3 R0 \5 s
Try visiting the site's homepage.- u- ^; t0 H9 H7 Y3 I) ?0 b$ V; M
ERR_BLOCKED_BY_XSS_AUDITOR
作者: 北美生活网 时间: 2017-4-14 20:43
Discuz!X3.1-X3.2后台admin.php防止直接恶意访问% l$ M1 S* \8 m M, l" b$ C
& r8 E# x: ?: p9 [' y! b+ ~
各位站长应该都知道Discuz!程序的后台是“域名/admin.php”,在站长朋友没有设置任何保护措施的情况下,任何人、任何一台终端都可以随意的访问到在php虚拟主机上运行的Discuz的后台,那么黑网站的第一步就不费吹灰之力的完成了,这里给大家分享一下如何防止Discuz!X3.1-x3.2后台被恶意访问,为了防止程序后台被恶意访问,大家可以做一下修改:1 K% `; S4 a7 A# I5 X; i
在网站根目录找到admin.php,找到如下代码:" F+ x2 z2 U w5 Z
$discuz->init();7 h8 J9 k8 l# ]5 z$ Q2 _8 }
接下来在此行代码下面添加如下代码:
2 p! h& K# f& Y9 m% Y2 _/ I, ?if(!$_G['uid'] || !getstatus($_G['member']['allowadmincp'], 1)) {
% @# f, F0 W# v' B/ Eheader('Location: /');. }4 P% B2 z* d: ?, A, r
}
: X" Z1 {( a# Z& x5 z! g6 R4 X, t保存上传覆盖就搞定。这样就实现了非管理员全部返回网站根目录。
o1 b! L s2 _如果管理员要登陆后台,直接在前台会员登陆界面登录就行了!
| 欢迎光临 北美网备份站 (http://beimeilife.duckdns.org/) |
Powered by Discuz! X3.2 |








